Your BYOD and Contractor Workspace
Secure Enterprise Browser Built for Productivity
Users access applications from any devices anywhere.
Everything your employees and third-party contractors need is securely built-in—eliminating insider threats while enabling effortless work.

Modern BYOD Workforce
Secure your
BYOD workforce
Full Enterprise Security—on any device,
with no MDM required
Your workforce is more mobile than ever. Employees, contractors, and third parties
are logging in from everywhere—on personal laptops, tablets, and phones.
With Mammoth Enterprise Browser, you can extend Zero Trust protection to
unmanaged devices without sacrificing control, compliance, or user experience.

The modern workforce lives outside the perimeter
You can’t control every device. But you still need to:
- Protect sensitive enterprise data
- Comply with security and privacy mandates
- Ensure users don’t leak info to GenAI tools or unapproved apps
- Respond to Zero Day threats—without MDM or VDI overhead
Mammoth makes that possible.
Secure access, anywhere, with nothing to install or manage on personal endpoints.
The Mammoth Solution
True zero trust for BYOD users
Mammoth turns any browser session—on any device—into a fully governed, enterprise-controlled experience.
Launch apps in an isolated, enterprise-only browser
Restrict copy/paste, downloads, uploads, and print
Auto-watermark and record high-risk sessions
Block access based on identity, device type, or location
Enforce DLP and GenAI usage policies in real time
You stay in control—without controlling the device.
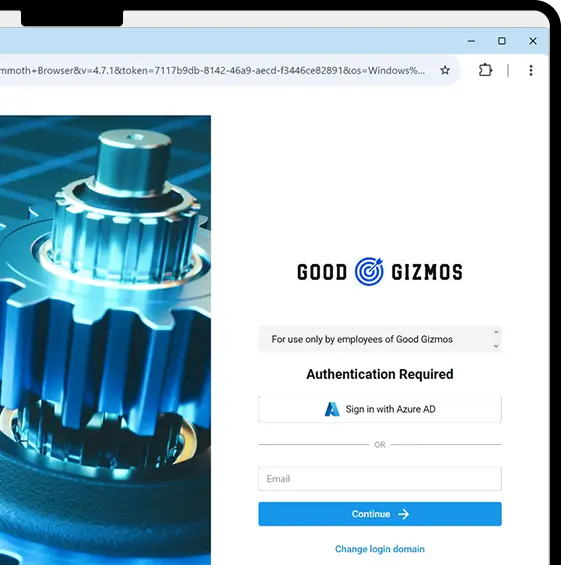
Secure Browser with Data Isolation
- Ensures device trust and data isolation to keep sensitive information off personal devices
- Protects against phishing attacks and malicious sites with robust security measures.
- Simple to use—download the browser and start working securely in minutes.
- Delivers peace of mind without complexity in a seamless, secure browsing experience.
Works on personal laptops, tablets, and mobile phones
Whether users are at home, on-site, or on the move, Mammoth enables:
- Secure SaaS access with no risk of data leakage
- Native Zero Trust protection for BYOD environments
- Seamless browser sessions across Windows, macOS, iOS, and Android
- Session-based governance, even on unmanaged hardware
It’s the easiest way to secure your distributed workforce—without introducing friction.

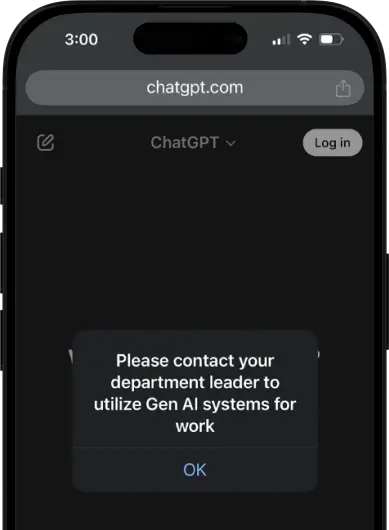
GenAI access— blocked before it becomes a breach
Worried about employees uploading customer data to ChatGPT or copying IP into Gemini? Mammoth prevents:
- Unauthorized GenAI use from unmanaged devices
- Uploads of source code, PII, or business documents to LLMs
- Shadow IT behaviors on browsers you don’t manage
- GenAI access entirely—or enforces visibility and control per policy
Zero Trust means you define the boundaries—no matter where
the user sits.
Mammoth is built for
Fully remote companies
Secure distributed teams with full visibility and control — no matter where they work or what device they use.
Contractors and temporary staff
Grant instant, time-bound access to apps and data without provisioning laptops or relying on VPNs.
Offshoring and BPO operations
Enforce data policies across outsourced teams while maintaining compliance and auditability.
Field teams, advisors, customer-facing reps
Enable secure, lightweight access to critical apps — even on mobile or personal devices.
Regulated industries(Finance, healthcare, and manufacturing)
Meet strict compliance requirements with built-in controls for data access, sharing, and retention.

Use Case
Enabling Remote BYOD Access for a Global Pharma Company
A global pharmaceutical firm needed to enable secure access to clinical and operational systems for over 2,000 researchers, partners, and auditors across unmanaged devices.
With Mammoth, they:
- Enabled secure BYOD access with no MDM or VDI
- Blocked unauthorized uploads to GenAI platforms
- Applied policy-based session control based on user identity
- Maintained compliance across 5 continents
Fast to Deploy. Simple to Scale.
No VPN. No endpoint agent. No infrastructure overhaul.
Step 1
Plug into your identity provider
(Okta, Entra ID, Ping)
Step 2
Start with a single app or user group
Step 3
Expand to cover your entire hybrid workforce
Your users get fast, frictionless access. You get full control and peace of mind.
Ready to secure your BYOD Workforce?
Let’s show you how Mammoth Enterprise Browser delivers Zero Trust for BYOD—without complexity.