Secure the Browser. Secure the AI.
Download the Enterprise AI Browser Security Checklist — a practical guide to protecting your organization from the next generation of AI-driven cyber threats.
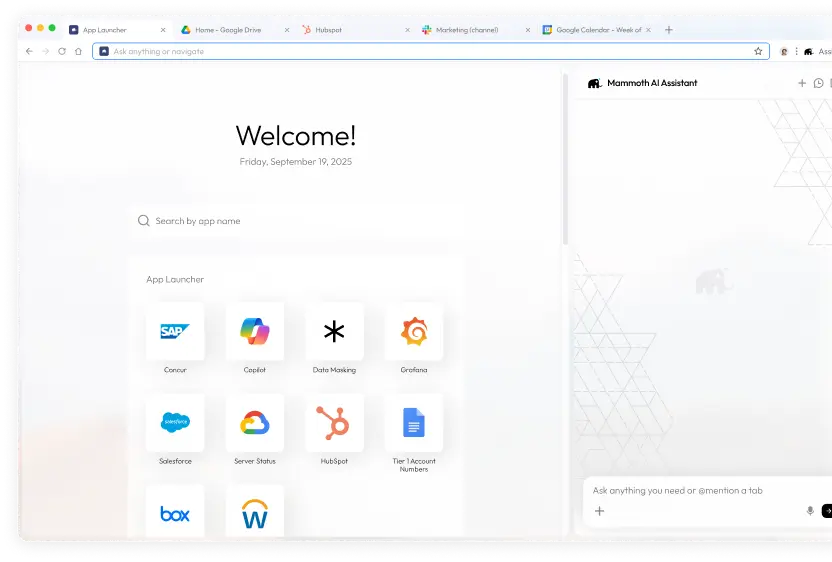

The Browser Has Become the New Endpoint
AI is no longer confined to standalone tools — it’s built into browsers, copilots, and productivity apps your employees use every day.
But with that convenience comes exposure.
Large Language Models (LLMs) can now access sensitive data, interpret untrusted web content, and even execute hidden instructions — creating risks traditional endpoint security can’t detect.
The result: Prompt injection, Shadow AI, and invisible data leakage from inside the browser session.
Inside the Checklist
This 8-page checklist maps the OWASP LLM Top 10 (2025) risks to practical enterprise controls.
It’s designed for CISOs, security architects, and IT leaders who want to stay ahead of the AI threat curve.
With Mammoth, they:
- Identify AI-browser attack surfaces linked to prompt injection and Shadow AI
- Align browser security posture with OWASP LLM Top 10 (2025)
- Protect data through AI isolation, DLP, and identity enforcement
- Audit and log AI activity for compliance and forensics
Includes:
A full 8-point security checklist covering:
- Identity & Access Control
- Endpoint Posture
- Data Loss Prevention
- Session Security
- AI Sandboxing
- Audit Logging
- User Experience
- Privileged Access
Built for the Enterprise
Security Leader
CISOs & Security Executives
Audit AI risks across browsers and devices.
Security Architects & DevSecOps
Integrate AI isolation into your zero-trust stack.
Compliance & Governance Teams
Validate controls for LLM data handling.
IT Managers
Govern AI-assisted workflows without blocking innovation.
Powered by Mammoth Cyber
Mammoth Cyber’s Enterprise AI Browser is built for organizations embracing AI responsibly — combining productivity with data protection.
With features like inline DLP, AI prompt sanitization, and sandboxed LLM isolation, it ensures that generative AI tools remain compliant, visible, and secure.
Learn how the browser itself becomes your zero-trust control plane.

Download the Enterprise AI Browser Security Checklist
Understand the top 10 AI-browser risks — and the controls you can deploy today.
