Secure work from any device

A browser built for control and compliance.
App access control
Enforce granular, context-aware access policies across web applications. Define who can access what — based on identity, device, location, and risk level — with full support for conditional access, time-based controls, and app-specific restrictions.
Session visibility
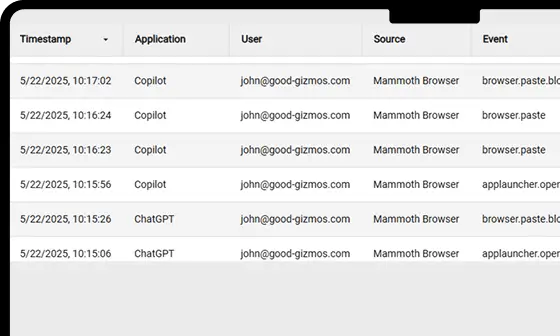
Gain real-time visibility into browser sessions across your organization—including unmanaged or shadow IT usage. Monitor user behavior, detect anomalies, and investigate incidents faster with rich, event-level logging — all without relying on third-party proxies or desktop agents.
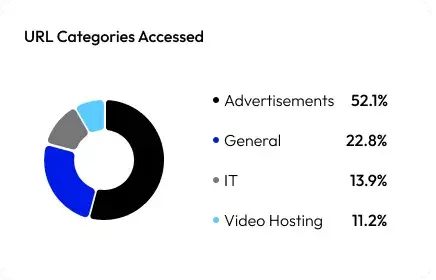
Data Access Insight
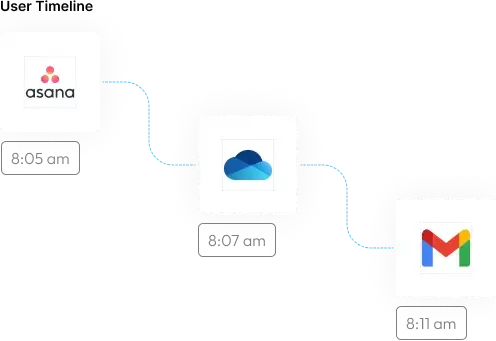
Seamless Integration
with Your Identity Stack
Connect the Mammoth Enterprise Browser to your existing authentication infrastructure in minutes. Whether you’re using Okta, Azure AD, or another SAML-based SSO provider, Mammoth enforces your access policies while adding an extra layer of session and data control — all without interrupting the user experience.

Securing workforces across industries
“The best thing about the Mammoth Cyber solution is that it is so seamless for our remote employees.”

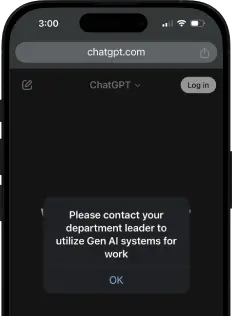
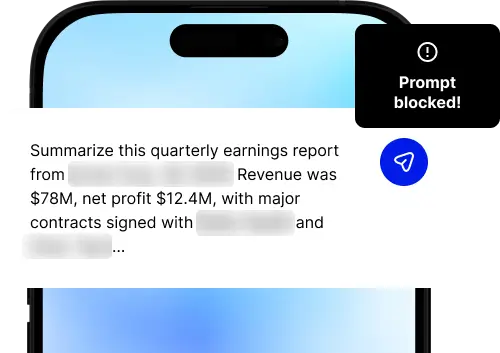
Secure your LLM workflows before prompt leakage happens
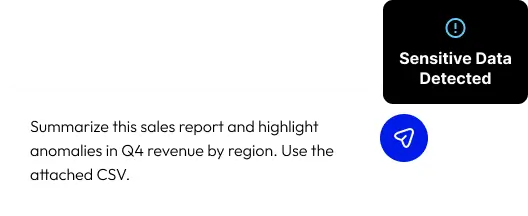
AI Input/Output Scans
Automatically scan data transfers to and from GenAI for sensitive content and to ensure data compliance.
Securing Data Leakage

SaaS AI App Blocking
GenAI without the data risk
Legal
Customer Support
R&D
- Prompt Visibility
- AI App Blocking
- Deployment
- Tamper Resistance
- Full, real-time prompt inspection
- Granular blocking by domain, user, role
- Native browser experience, no agents
- Centralized and tamper-proof
- Limited — can’t always parse encrypted data
- Works if routed; bypassable on local apps
- Requires network routing changes
- Depends on consistent routing
Mobile access without compromise
Secure Data Isolation
Safe Internet Browsing
Private App Access
Powering Secure Work Anywhere
BYOD
Enable employees and contractors to use their own devices securely. Enforce access controls and data protection without requiring MDM or installs.
Field Mobile Access
Contractor & Partner Access

Why Mammoth Cyber?
Mammoth Enterprise Browser fixes security gaps with endpoint access posture management, unifies control for all user roles and devices, and secures the browser—employees’ weakest link—against attacks and data leaks. It ensures safe access for contractors, partners, remote developers, and unmanaged devices without complexity.
Fix the Security Gaps in Access
Unified Control
Increase with Business Agility
Secure Contractors, Partners, Remote Developers, and Unmanaged Devices
“The best thing about the Mammoth Cyber solution is that it is so seamless for our remote employees. They just open the browser and go. On the security side, we really like the fact that this helps move our zero-trust initiative forward.”
FAQ
Why is browser security more critical now than ever?
Browsers are the primary interface for SaaS, cloud tools, and AI, handling 80% of enterprise data and facing phishing, XSS, and insider threats. Mammoth Cyber’s endpoint-based security uses DOM monitoring and zero-trust policies to block attacks, reducing breach risks by 40% across managed and unmanaged devices.
Can Mammoth Cyber replace or reduce our need for VDI?
A: Yes, Mammoth replaces VDI for web apps with secure browser policies, cutting IT costs by 60% and latency by 30%. It supports BYOD, ensuring secure access for remote workers without virtualized infrastructure.
How does Mammoth secure AI tools like ChatGPT and prevent data leaks?
Mammoth’s AI-aware DLP monitors browser and endpoint traffic, allowing trusted AI models while blocking unauthorized ones. Features like watermarking and copy-paste blocking prevent data leaks, ensuring GDPR compliance.
What makes Mammoth different from SASE or SWG solutions?
Mammoth Enterprise Browser ensures endpoint security with device trust and data isolation, enabling secure copy-paste within the trust circle while blocking phishing and malicious sites. Download for instant access without SASE/SWG latency, proxies, or SSL encryption/decryption.
How do you control browser behavior on unmanaged or BYOD devices?
Mammoth Enterprise Browser enforces secure browsing on BYOD without MDM. Centralized policies ensure compliance, with 50% faster deployment for contractors and remote workers.
What are some unique security controls Mammoth enables?
Mammoth offers session recording, copy-paste blocking, watermarking, screen-share prevention, and data masking. These reduce breach risks by 40%, ensuring ISO 27001 compliance on managed and unmanaged endpoints.
Secure your workforce, wherever they work.
Enable safe, seamless access across devices and locations.


