In today’s digital-first world, enterprises rely on web applications to manage and display sensitive data, from customer records to financial reports.
- May 31, 2025
How Mammoth Enterprise Browsers Secure Web Data with Advanced Data Masking
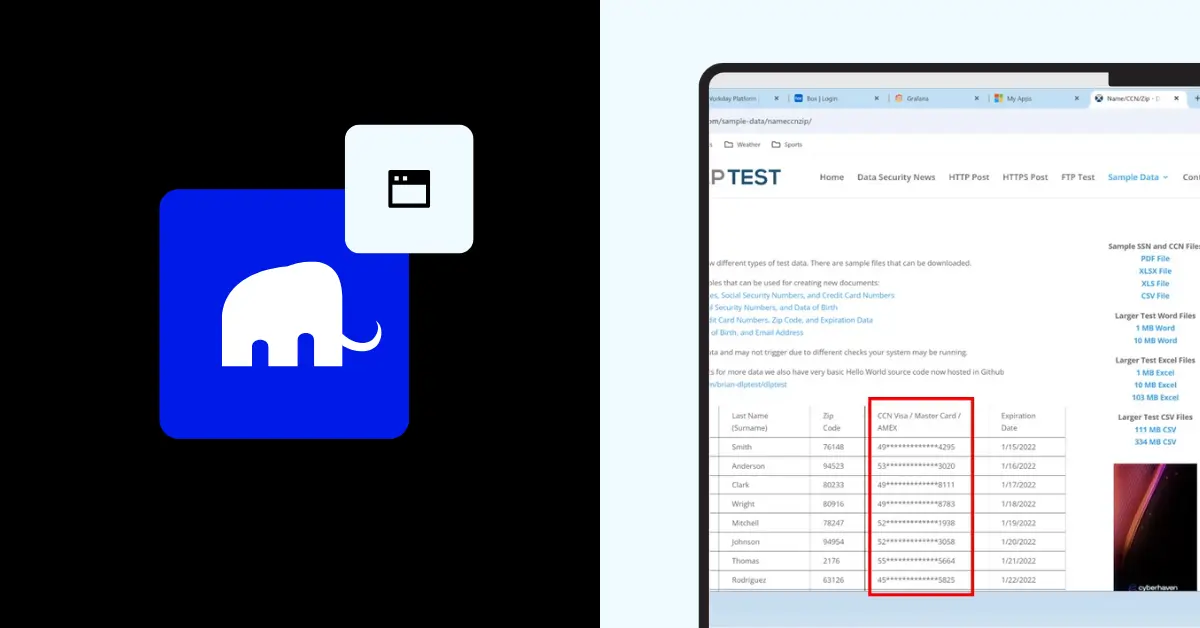
However, this reliance comes with a critical challenge: ensuring that sensitive information, such as Social Security Numbers (SSNs) or credit card details, is only visible to authorized users. Without proper safeguards, organizations risk data breaches, compliance violations, and reputational damage. Mammoth Enterprise Browsers address this challenge with cutting-edge data masking technology, seamlessly integrated into the browser core to deliver real-time protection without compromising user experience.
This article explores why traditional solutions fall short, how Mammoth’s innovative approach revolutionizes web security, and the benefits of browser-based data masking for enterprises striving to stay secure and compliant.
The Growing Risk of Exposed Sensitive Data
Web applications are the backbone of modern enterprises, powering everything from customer service portals to internal dashboards. However, many of these applications lack granular access controls, exposing sensitive data to unauthorized users. This creates significant risks, including:
- Customer Service Vulnerabilities: Support agents often access customer profiles containing SSNs or other personal data, even when such details aren’t necessary for their tasks. This overexposure increases the risk of accidental leaks or insider threats.
- Financial Data Breaches: Displaying full 16-digit credit card numbers in financial reports can lead to misuse or non-compliance with standards like PCI-DSS.
- Compliance Challenges: Regulations such as GDPR, HIPAA, and PCI-DSS require strict control over who can view sensitive data. Failure to comply can result in hefty fines and legal repercussions.
Traditional Data Loss Prevention (DLP) solutions primarily focus on protecting files, leaving web-based data vulnerable. Extension-based masking tools attempt to bridge this gap by modifying the browser’s display layer, but they often fall short. These tools may briefly display sensitive data before masking it, creating a window of vulnerability that malicious actors can exploit. Additionally, extensions can be bypassed or disabled, undermining their effectiveness.
Mammoth’s Revolutionary Data Masking Solution
Mammoth Enterprise Browsers take a fundamentally different approach by embedding data masking directly into the browser core. This ensures that sensitive data is protected from the moment a web page begins to render, eliminating the risks associated with traditional solutions. Unlike extensions that operate superficially, Mammoth’s technology is built for enterprise-grade security and compliance.
Key Features of Mammoth’s Data Masking Technology
- Real-Time Data Masking: Mammoth identifies and masks sensitive information—such as SSNs, credit card numbers, or health records—as the web page loads. Unauthorized users see only masked data (e.g., “XXX-XXX-1234” instead of a full SSN), ensuring no exposure.
- Seamless User Experience: For authorized users, the masking process is invisible, preserving the functionality and usability of web applications. This balance of security and efficiency is critical for maintaining productivity.
- Compliance-Ready Design: By restricting access to sensitive data based on user roles, Mammoth helps organizations meet stringent regulatory requirements, including GDPR, HIPAA, and PCI-DSS.
- Customizable Role-Based Access: Administrators can define granular access policies, ensuring that employees see only the data necessary for their roles.
How Mammoth Compares to Traditional Solutions

By integrating data masking at the browser level, Mammoth eliminates the vulnerabilities of extension-based tools and extends protection beyond the file-centric focus of traditional DLP solutions.
Benefits of Browser-Based Data Masking
Mammoth’s innovative approach delivers measurable benefits for enterprises:
- Enhanced Security: Sensitive data is masked before it reaches the screen, preventing unauthorized access or accidental exposure.
- Accurate Role-Based Access: Dynamic masking ensures that employees see only the data their roles permit, reducing the risk of insider threats.
- Regulatory Compliance: Mammoth’s technology aligns with global data protection standards, helping organizations avoid costly penalties.
- Elimination of False Security: Unlike extensions that may briefly display sensitive data, Mammoth’s solution ensures continuous protection, providing true peace of mind.
Real-World Impact: A Customer Service Use Case
Consider a large e-commerce company with a customer service team handling thousands of inquiries daily. Their web-based support portal displays customer profiles, including SSNs and payment details. Without proper controls, agents can view full SSNs, even when only the last four digits are needed to verify identity. This overexposure risks data leaks and violates PCI-DSS and GDPR requirements.
By implementing Mammoth Enterprise Browsers, the company configures role-based access policies to mask SSNs for all support agents except senior supervisors. When an agent accesses a customer profile, the SSN appears as “XXX-XXX-1234,” while supervisors with clearance see the full number. The masking happens instantly at the browser level, ensuring no sensitive data.
Mammoth Cyber
Ready to leave VDI behind?
Explore how the Mammoth Enterprise Browser secures GenAI development workflows and accelerates developer velocity—without compromise.
Don’t miss these
Subscribe to our
monthly newsletter
Be the first to know what’s new with Mammoth Cyber. Subscribe to our newsletter now!
Follow us
© 2025 Mammoth Cyber. All rights reserved.
EULA | Terms | Privacy Notice