How a Global Financial Holding Company Uses Mammoth Browser’s “Trust Circle” to Prevent Sensitive Data Leakage

Financial institutions face a unique and escalating challenge: how to safeguard highly sensitive data while enabling tens of thousands of employees and contractors to work efficiently across a complex ecosystem of applications, workflows, and devices. Traditional controls—such as VPNs, endpoint agents, virtual desktops, and cloud access security brokers—provide partial visibility but often fail to control the most vulnerable layer of modern work: the browser itself.
The Hidden Risks of AI Browsers — and Why Security Must Come First
Artificial intelligence is transforming how we work — and once again, the browser is at the center of it all. With over 85% of employees’ work happening inside the browser, the industry is now embedding AI assistants directly into it, giving rise to a new generation of AI browsers that promise smarter, faster, and more connected work.
Announcing Mammoth Enterprise Browser for Android
We’re excited to announce that Mammoth Enterprise Browser is now available on Android phones and tablets. Users can securely access internal company web applications using their personal Android devices, without relying on a VPN or a desktop PC.
Mammoth Cyber’s Vision To Reimagine The Enterprise Browser
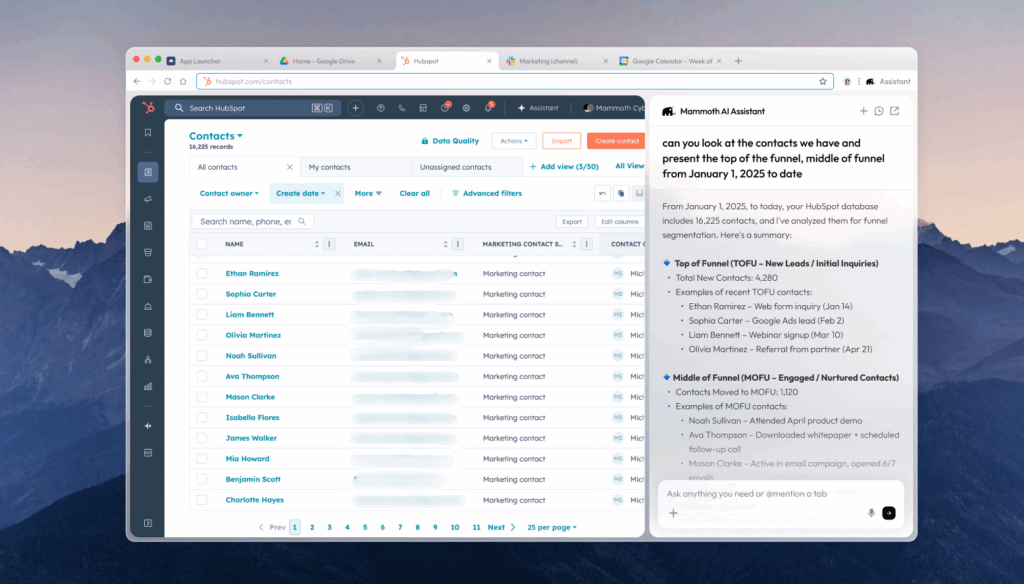
Enterprise browsers have long served as an organizational control point, complimenting other security solutions delivered as a service and through clouds, but they are rapidly evolving for an important reason. They are the user interface for modern AI applications, and IT operations teams are struggling to keep pace with the rapid adoption of these tools. To address the need for safe and secure generative AI usage, enterprise browsers are quickly morphing into purpose-built offerings to enforce AI runtime security, integrate business context, and infuse zero trust least privileged access.
Enterprise AI Browsers: Rocket Fuel for the Business—And a Loaded Gun Without Zero Trust

“Mammoth Cyber isn’t promising a silver bullet—and that’s a good thing. Instead, it offers a pragmatic, integrated approach for organizations that are serious about Zero Trust.”
Deterring Enterprise AI Risks with Enterprise Browser

“In the AI era, trust is a vulnerability. Enterprise browsers empower us to protect critical systems with relentless verification and real-time control.”
How Mammoth Cyber is Enabling Zero Trust in a Cloud-Centric World

“Mammoth Cyber isn’t promising a silver bullet—and that’s a good thing. Instead, it offers a pragmatic, integrated approach for organizations that are serious about Zero Trust.”